15 First Class Spear Phishing Vs Phishing
Ad Fast Light and Easy to Use. Ad Block Unsafe Links Downloads Email Attachments with AVG Free Antivirus.

Spear Phishing Who S Getting Caught Infographic Firmex Resources
Midnight to 2 am.

15 First Class spear phishing vs phishing. COLONEL ARBUTHNOT British subject Berth No. This sophisticated technology means that phishing emails have become an automated process meaning they are increasingly accurate and therefore believable. Reuters reported Israeli Defense is the latest illustrious victim of the Spear Phishing Attack and hackers penetrated into an Israeli defense ministry computer using a malicious email as a vector.
Revenge as he was John Armstrongs best friend. CYRUS HARDMAN American subject Berth No. The second-stage script disables Powershell script logging to avoid leaving traces and then downloads the final Powershell Empire agent payload which allows fileless control of the compromised systems over an encrypted.
In this 60-minute webinar we deep-dive into the social engineering techniques currently being used against power grid workforces and determine how these are likely to develop in the next 2-3 years. We review a range of cyber awareness programmes cyber hygiene approaches and incident response strategies that are helping proactive power grid cybersecurity leads to outsmart and thwart. Alibi Midnight to 2 AM.
And foreign government agencies and think tanks this. The tool is designed to discover phishing email attacks spear-phishing attacks and zero-day attacks. Ad Block Unsafe Links Downloads Email Attachments with AVG Free Antivirus.
Midnight to 2 am. A single person is targeted and the information in the email is tailored specifically to them which increases the likelihood that theyll respond. Whaling Read Post The difference between phishing spear-phishing and whaling attacks is on the scale of personalization.
Researchers found that the technique used to obfuscate and decrypt the malicious code is same as used in the original Olympic Destroyer spear-phishing campaign. If an employee mistakenly clicks on a malicious link the hacker could pilfer the account details and install malware onto the system in an effort to infiltrate corporate networks potentially making business data sensitive information and security at risk. Revenge as he was John Armstrongs best friend.
Between July 2015 and December 2015 he targeted online food delivery firm Just Eat using a scam in which customers received a bogus email offering a voucher in return for answering questions. Substantiated by MacQueen and conductor Evidence against him or suspicious. Went to his own compartment and did not leave it.
Went to own compartment and did not leave it. There have been reports of PayPal. Went to his own compartment and did not leave it.
Spear Phishing This hacking method takes a more refined and personalized approach which is much more convincing than generic phishing. Improved Security for Your PC. Substantiated by MacQueen and conductor Evidence against him or suspicious circumstances Pipe-cleaner.
Powered by unsupervised machine learning Cyber AI platforms come to understand how. Get the Essential Free Protection That Wont Let You Down. Knowbe4 offers a Free Phishing Security Test service that allows you to find out what percentage of your employees are Phish-prone.
To recognize the latest threats SpamTitan uses a mixture of machine learning and Bayesian analysis to identify new attacks. Talked with MacQueen till 130. Improved Security for Your PC.
Detecting spear phishing campaigns requires a platform approach to cyber defense as opposed to siloed email-specific solutions. Substantiated by MacQueen and conductor Evidence against him or suspicious. Its thought that 2020 will see more phishing emails masquerading as.
Talked with MacQueen till 130. The powerful email protection against zero-day threats is excellent for minimizing exposure towards emerging email threats. BOSTON AP The state-backed Russian cyber spies behind the SolarWinds hacking campaign launched a targeted spear-phishing assault on US.
Talked with MacQueen till 130. In 2020 phishing is becoming an increasing threat because of cyber criminals access to machine learning systems. Spear-Phishing Read Post Spear-phishing is a targeted attack that uses fraudulent emails texts and phone calls in order to steal a specific persons sensitive information.
Get the Essential Free Protection That Wont Let You Down. One prominent study found that among 150000 phishing emails sent for the experiment almost half of recipients clicked on the emails scam link within the first hour. Ad Fast Light and Easy to Use.
Aviv Raff Chief Technology officer at Seculert confirmed that an Email with a malicious attachment that looked like it had been sent by the countrys Shin Bet Secret Security Service. Spoofing and phishing are schemes aimed at tricking you into providing sensitive informationlike your password or bank PINto scammers.
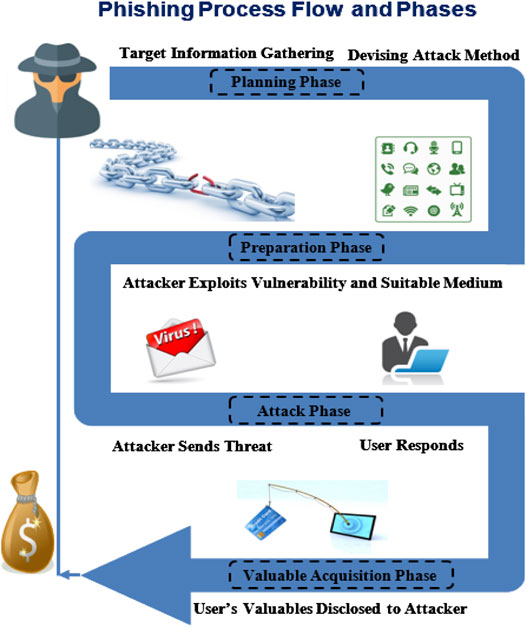
Frontiers Phishing Attacks A Recent Comprehensive Study And A New Anatomy Computer Science

Spear Phishing Statistics From 2014 2015 Infosec Resources

Spear Phishing Is A More Sophisticated And Dangerous Form Of Phishing Understand The Differences Phishi Spear Phishing Online Safety Student Encouragement

Even If You Re Wise To Phishing Spear Phishing Could Still Fool You Computer Security Cyber Security Cyber Safety
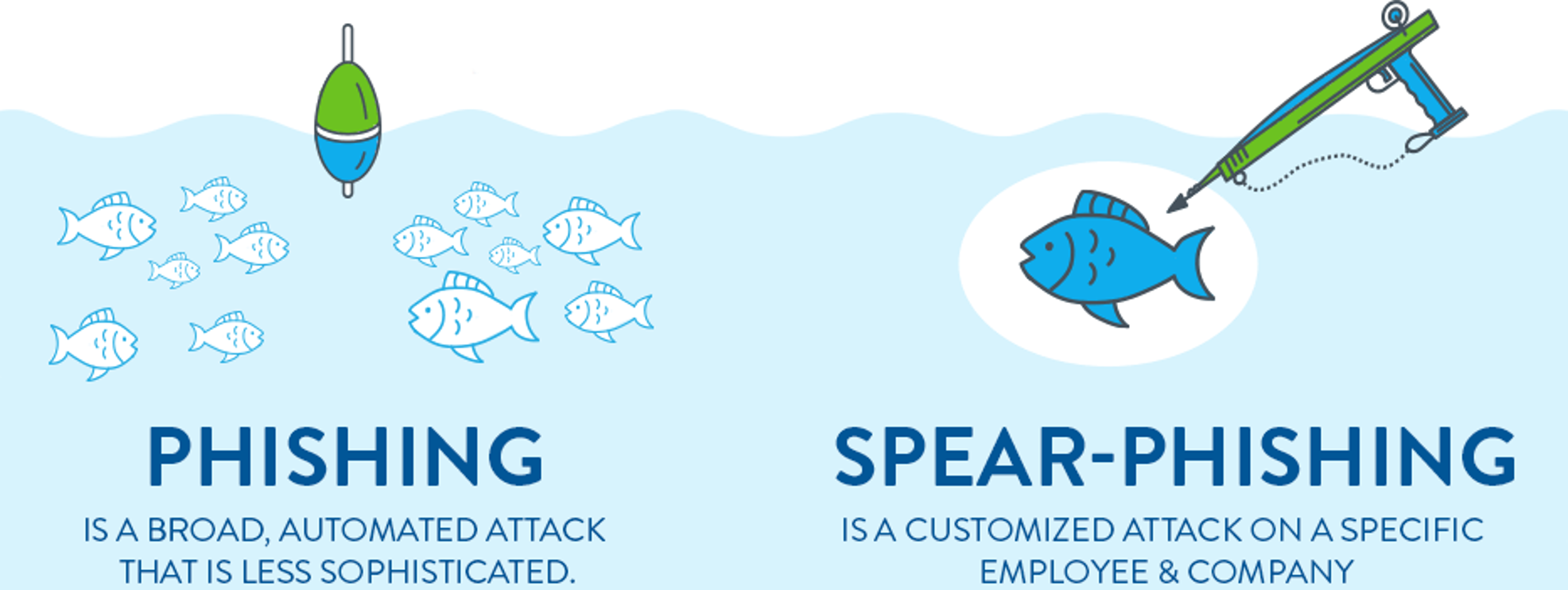
There Is Not Any Longer This Sort Of Factor As Laptop Safety Webdesignwp

Spear Phishing And Whaling Infosec Resources

People In Spear Condition Saw This Comic Strip Download Scientific Diagram

10 Phishing Email Examples You Need To See

Spear Phishing Statistics From 2014 2015 Infosec Resources
Schooling A Sea Of Phish Part 1 How Office 365 Advanced Threat Protection Helps Stop Spear Phishing Microsoft Tech Community

Spear Phishing Statistics From 2014 2015 Infosec Resources

Spear Phishing Takes Advantage Of Your Employees Trust Duocircle
Timeline Of Spear Phishing Experiment Download Scientific Diagram

Spear Phishing Statistics From 2014 2015 Infosec Resources

Pdf On The Need For New Antphishing Measures Against Spear Phishing Attacks

Spear Phishing Statistics From 2014 2015 Infosec Resources

End User Infection Through Spear Phishing Download Scientific Diagram
Schooling A Sea Of Phish Part 1 How Office 365 Advanced Threat Protection Helps Stop Spear Phishing Microsoft Tech Community

The Ecosystem Of Phishing From Minnows To Marlins Digital Shadows

